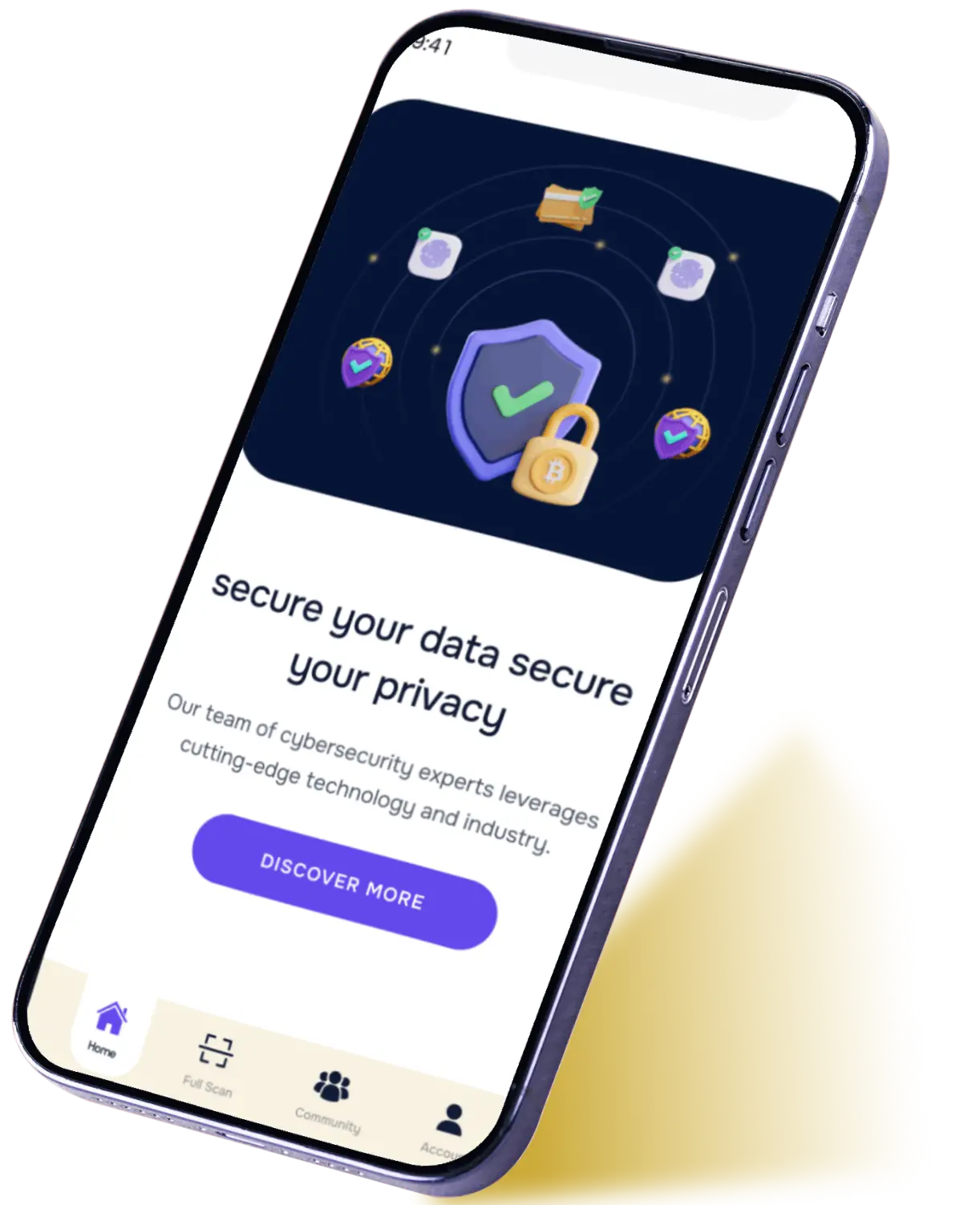
cyber security app
We protect your digital world from threats
Our team of cybersecurity experts leverages cutting-edge technology and industry best practices to provide proactive defense measures and ensure maximum protection .



Trusted partners :
Regular software updates
Outdated software can contain vulnerabilities that cybercriminals can exploit.
Network security configuration
Secure networks, firewall settings, encryption ensure robust network security.
Scheduled data backups
Automated data protection through scheduled and consistent backup routines.
Strong authentication mechanisms
Explanation of the importance of establishing security policies within organizations.

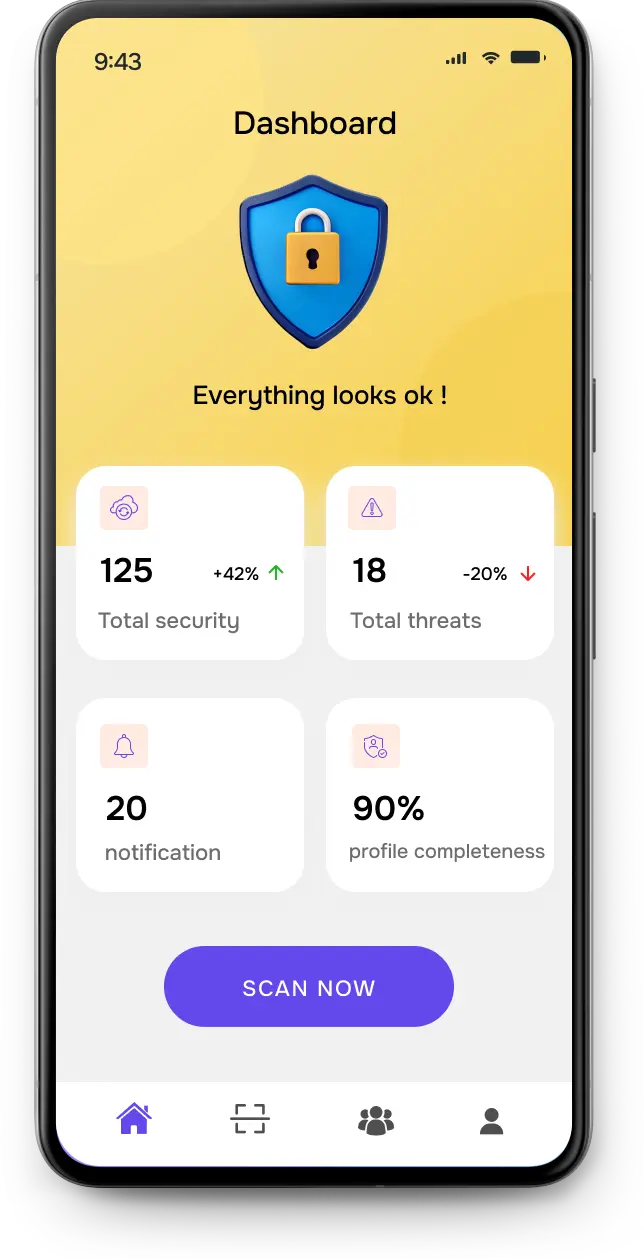
cyber security app
Defending your digital realm, one byte at a time
Ensure that your server’s operating system, applications, and software are regularly updated with the latest security patches and fixes.
Malware analysis
98%
Troubleshooting
85%
Patch & update management
92%
why choose us
We focus on fraud detection and prevention of all data
100% Cyber security
Encrypt data, update software, use strong passwords, stay vigilant.
Infrastructure security
Ensure robust infrastructure security for data protection and compliance.
Risk management
Identify, assess, mitigate: Cyber risks demand strategic risk management.
Magnification issues
Magnification distorts content, blurring details and reducing overall clarity.
security app
Take control of your projects with vonix
Stay on top of your projects with our intuitive task organization feature. Break down projects into manageable tasks.
Incident response & recovery
We strive to provide the highest level of protection possible for our clients.
Securing networks everytime
We work tirelessly to mitigate risks and defend against cyber attacks.
- New features
0
+
- App download
0
%
- Active users
0
k
- Positive rateing
0
%
security app
Cyber information sharing & collaboration program how to combating cyber crime
Best practices for maintaining security online, such as using strong passwords, enabling two-factor authentication, and keeping software updated.
App Store
Google play

Cyber crime16 February 2024
Secure cyber Insights

Cyber crime16 February 2024
